
AI models are valuable intellectual property (IP). They often represent years of work, money, and expertise. If these models are stolen, copied, or misused, companies lose their competitive edge and revenue.
At PACE Anti-Piracy, we focus on protecting software that runs on devices outside the cloud–like desktops, phones, and IoT devices. We recently launched Fusion AI to protect Embedded AI running on customer premises, within desktop applications, and at the edge.
This article explains why Embedded AI is growing in importance, the risks of model theft, and how to keep your models safe.
Most people think of AI as something that runs in the cloud. You type in a prompt, send it to a server, and get an answer back.
However, there are many use cases where it makes more sense to run at the edge with the model embedded into software running locally to the user or the data. This is called Embedded AI.
There are a few reasons for running AI at the edge:
AI models take a different form from traditional algorithms.
Traditional algorithms are coded (e.g., in C++) as logical sequences and compiled into machine code that executes on the edge device.
AI takes many forms. The development methodology will depend on the form of AI being implemented. Something like a rule engine or knowledge graph will be coded like a traditional program, whereas statistical approaches, like Machine Learning (ML) and Large Language Models (LLMs), require more complex implementations.
The complexity of statistical models means they are generally developed in a framework (e.g., PyTorch), much like game developers build on top of Unreal Engine and Unity to avoid having to reinvent the complex building blocks.
The framework is generic code, with the valuable IP contained in the model that runs on the framework. Models are typically a mix of data and interpreted code (e.g., Python that is deployed as source code). This makes them extremely easy to lift, analyze, and steal.
The interpreted code defines the structure or architecture of the model. Basically, how the different algorithms that make up the model are connected together.
The data defines the statistical “weights” that are calculated by training the model and applied throughout its execution as it processes the input data to reach a conclusion.
For more performant models and on resource-constrained devices, compiled code may be used in development to increase performance. This makes development much harder, and out of the comfort zone of data scientists, so it’s rare.
While there are many threats to AI at the edge, the risk of IP being stolen is the one that holds back many companies. They don’t want their hard work falling into the hands of researchers, competitors, or criminals.
For teams building embedded AI products:

Stopping the AI models from being stolen is a code-protection challenge. You need to stop reverse engineering and lifting of the model. It should not be possible to:
The model should be encrypted at rest. But real protection means using white-box cryptography at runtime to perform the decryption. A white-box is needed to protect decryption keys. Also, it will need to be securely anchored into the rest of the software so it all stays coupled to the developer’s use case.
White-boxes that are provided as developer toolkits, like PACE’s White-Box Works, allow solutions to be architected that tightly tie in with AI runtime. This minimizes any gaps where the model is in the clear between decryption and model initialization.
Strong runtime protection products, such as PACE’s Fusion, should be used to securely tie all the different components together – ensuring that the AI stays tied to the wider application’s use case. Runtime protection also stops a threat actor from attaching debuggers and other analysis tools to observe or manipulate the model at runtime.
AI models are valuable intellectual property, but when embedded into software applications, they face serious risks of theft and tampering. Running AI at the edge offers benefits like lower costs, faster response times, and stronger privacy, but it also makes models easier to copy or reverse engineer.
To protect both the technical work of developers and the business value that product managers depend on, companies must secure models at rest, during runtime, and in use. With tools like Fusion AI, organizations can encrypt models, block attacks, and tightly connect protections to their applications–ensuring AI remains both safe and commercially viable.
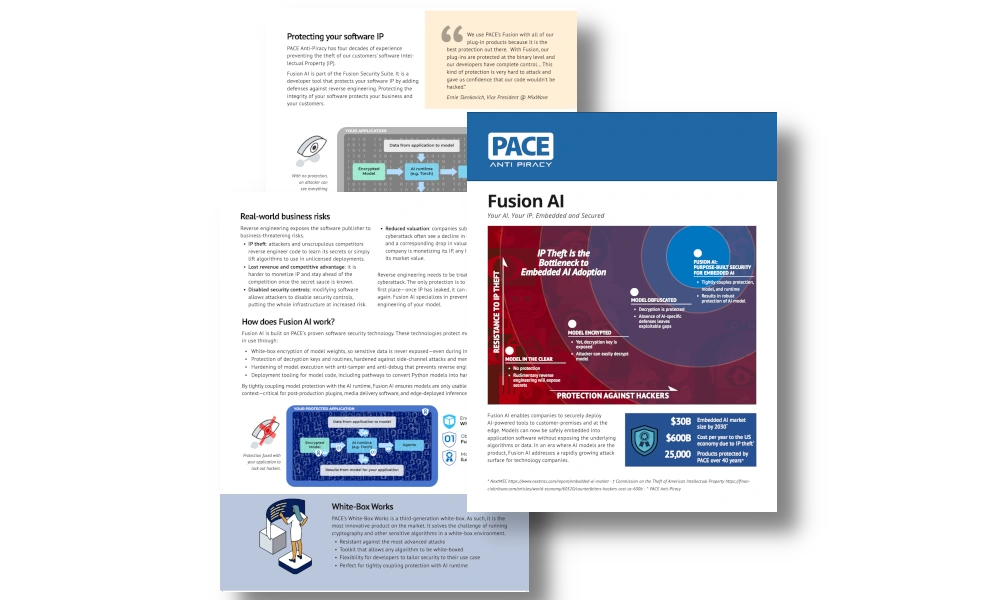
Download the Fusion AI product brochure to learn more about how PACE protects your AI models and allows you to maximize their value.
Want to learn more about protecting your Embedded AI? These articles are a good place to start:
Or reach out to PACE to discuss how we can secure your AI models when they are embedded into software applications.